Join the fight to regain our personal private data rights..........
Most do not know it, but your private personal data is a commodity which thousands of companies are earning billions off of, but did you give your permission? Most don't have a clue, but the PrivacyArmy does, and so will you when you register.
How do we stop it, simple, under commercial law if you contract with an entity, such as we have established, and you do not want your personal private date illegally violated, then we as a poweful group can initiate a class action against any company who uses our data again.
We have a patent pending legal strategy to recoup billions from this illegal activity of selling our personal private data to other companies. We will not only sue the companies who are selling our data, but we will also sue those who purchase it, and this includes 30,000 companies we have identified to date who are selling, while hundreds of thousands are purchasing our data.
If you remember the tobacco class action suits, you will get an idea of how many hundreds of millions there are at stake. WE, as registered members will pool all proceeds from all class action suits won and devide it equally amoung members. The potential is enormous, and with our press releases soon to begin, get positioned TODAY.
We have arranged to have the same law firms who won tobacco suits working for us. We need to increase our associations registered membership to handle the millions of potential leads we will generate in press releases, and we will each be paid to assist these interested citizens to register and join the war against our rights be violated. With over 100,000,000 already registered on the DO NOT CALL list, don't think for a minute people are not concerned about their personal private data being violated. These same companies who no longer can call us on list means little, they still have our data and use it in mailings.
JOIN US TODAY and SECURE YOUR PERSONAL DATA TOMORROW.............
BETTER THAN ANY HYIP YOU WILL EVER LOSE MONEY IN.......................
Short term income is amazing, mid term even more amazing, but the potential long term class action suit proceeds will award each of us a lifetime of PASSIVE income, just like HYIPsters have promised over and over, but never delivered on. Time to WAKE UP PEOPLE.
Please visit our sponsors
Results 1 to 9 of 9
Thread: PRIVACY-RIGHTS-ARMY.com
-
21-08-2006, 03:48 PM #1Senior Investor


- Join Date
- Jul 2005
- Location
- FREEDOMLAND
- Posts
- 3,277
- Feedback Score
- 0
- Thanks
- 574
- Thanked 2,129 Times in 355 Posts
 PRIVACY-RIGHTS-ARMY.com
PRIVACY-RIGHTS-ARMY.com
-
Sponsored Links
-
21-08-2006, 03:50 PM #2Senior Investor


- Join Date
- Jul 2005
- Location
- FREEDOMLAND
- Posts
- 3,277
- Feedback Score
- 0
- Thanks
- 574
- Thanked 2,129 Times in 355 Posts
 Privacy-rights-army.com
Privacy-rights-army.com
UPDATE:
Updated:2006-08-21 08:46:12
Who’s Watching?
By ERIC PETERS
Big Brother will be watching you for sure by 2008 -- the year a proposed requirement that Event Data Recorders (EDRs) become mandatory standard equipment in all new cars and trucks will become law unless public outrage puts the kibosh on it somehow.
EDRs are "black boxes" -- just like airplanes have. They can record a wide variety of things -- including how fast you drive and whether you "buckle-up for safety." The National Highway Traffic Safety Administration (NHTSA) wants EDRs to be installed in every new vehicle beginning with model year 2008 -- on the theory that the information will help crash investigators more accurately determine the hows and whys of accidents.
But EDRs could -- and likely will be -- used for other purposes as well.
Tied into GPS navigation computers, EDRs could give interested parties -- your local cash-hungry sheriff, for example -- the ability to take automated ticketing to the next level. Since the data recorders can continuously monitor most of the operating parameters of a vehicle as it travels -- and the GPS unit can precisely locate the vehicle in "real time," wherever it happens to be at any given moment -- any and all incidents of "speeding" could be immediately detected and a piece of paying paper issued to the offender faster than he could tap the brake. That's even if he knew he was in the crosshairs, which of course he wouldn't. Probably they'll just erect an electronic debiting system of some sort that ties directly into your checking account -- since the paperwork could not keep up with the massive uptick in fines that would be generated.
What Do You Think?
If you think this is just a dark-minded paranoiac vision, think again. Rental car companies have already deployed a very similar system of onboard electronic monitoring to identify customers who dare to drive faster than the posted limit -- and automatically tap them with a "surcharge" for their scofflaw ways. While this inventive form of "revenue enhancement" was challenged and subsequently batted down by the courts, the technology continues to be honed -- and quietly put into service.
Already, 15-20 percent of all the cars and trucks in service have EDRs; most of these are General Motors vehicles. GM has been installing "black boxes" in its new cars and trucks since about 1996 as part of the Supplemental Restraint (air bag) system. Within a few years, as many as 90 percent of all new motor vehicles will be equipped with EDRs, according to government estimates -- whether the requirement NHTSA is pushing actually becomes law or not.
The automakers are just as eager to keep tabs on us as the government -- in part to keep the shyster lawyers who have been so successfully digging into their deep pockets at bay. EDRs would provide irrefutable evidence of high-speed driving, for example -- or make it impossible for a person injured in a crash to deny he wasn't wearing a seat belt.
Insurance companies will launch "safety" campaigns urging that "we use available technology" to identify "unsafe" drivers -- and who will be able to argue against that? Everyone knows that speeding is against the law -- and if you aren't breaking the law, what have you got to worry about?
It's all for our own good.
But if you get edgy thinking about the government -- and our friends in corporate America -- being able to monitor where we go and how we go whenever they feel like checking in on us, take the time to write a "Thanks, but no thanks" letter to NHTSA at DMS Web
-
22-08-2006, 12:51 AM #3Senior Investor + HDG


- Join Date
- Jun 2005
- Location
- USA, Flordia
- Posts
- 536
- Feedback Score
- 0
- Thanks
- 0
- Thanked 21 Times in 13 Posts

Its just more invasion of our privacy rights being taken away froms us. One little piece at a time. Pretty soon there will be nothing left.
Gator
-
22-08-2006, 01:49 AM #4Senior Investor


- Join Date
- Jul 2005
- Location
- FREEDOMLAND
- Posts
- 3,277
- Feedback Score
- 0
- Thanks
- 574
- Thanked 2,129 Times in 355 Posts
 Privacy-Rights-Army.com
How Many Times Have You Been Sold Today?
Privacy-Rights-Army.com
How Many Times Have You Been Sold Today?
"The Product is You." -- Adbusters Media Foundation__________________________________________________ ____________Profiling is the recording and classification of behaviors. Profiling has sparked an entire industry euphemistically labeled "Customer Relations Management (CRM) or "Personalization," according to Privacy and Consumer Profilingpublished by the Electronic Privacy Information Center.
Companies collect information derived from a number of resources to build comprehensive profiles on individuals in order to sell products and to sell dossiers on behavior. This is often done without notice or extending a choice to the individual to opt-out of the dossier building. These dossiers may be used by marketers for target advertising, and they may be sold to government for law enforcement purposes. Companies also "enhance" dossiers that they already own by combining or "overlaying" information from other databases.
Others are making billions by selling our private property! Our personal data has been defaulted to corporate America, credit card companies, government agencies, target marketers; ANYONE who wants to buy it! As a result we are increasingly being exposed to Identity Theft , Personal Harassment and Economic Damages.
"We the People"...are the Uncompensated SOURCE of Supply. Alone we are powerless. Commercial databases think they own our Names, Addresses, Phone Numbers, Financial Data, Customer Histories, Medical Records and much more. Alone, our personal data is not respected as our private property and is being bought and sold daily without our consent or compensation.
The Privacy Army has created a patent-pending new category of commerce for the global economy. The legal foundation is its economic cornerstone. Heretofore we have been unable to assert "ownership rights" of our personal data becaust courts have noted we have no proof that we've suffered financial damages because no one has been willing to pay us for our personal data. Individually our personal data is too small to have economic value.
With the patent-pending Privacy Army Business Model, however, we can pool, package and market our collective data assets as a Premium Value, one-of-a-kind mailing list. From one enlightened person to the next, we can demand our private property be removed from ALL commercial data bases and capture our rightful share of the billions that usurpers are being paid for our property. By "Inalienable Rights" the money belongs to us.
Get the full story how you can restore your personal privacy, be compensated for informing others how they can as well, and take charge of selling your own data!
National conference call: Mon/Tue/Thu - 9:20pm EST at: (620) 294-4000 PIN: 988055#
http://Privacy-Act-Facts.com
-
22-08-2006, 01:54 AM #5Senior Investor


- Join Date
- Jul 2005
- Location
- FREEDOMLAND
- Posts
- 3,277
- Feedback Score
- 0
- Thanks
- 574
- Thanked 2,129 Times in 355 Posts
 Privacy-Rights-Army.com
Privacy-Rights-Army.com
FOR IMMEDIATE RELEASE
August 14, 2006
TSA CONCEPT VIDEO SHOWS FUTURE RFID-ENABLED AIRPORT
Spychips in Passports May be Just the Start, Warn Privacy Advocates
RFID-laced passports may be just the start of an Orwellian airport
experience, warn privacy advocates and authors Katherine Albrecht and
Liz McIntyre as the nation braces for a rollout of the controversial
technology in passports this week.
They point to a U.S. Transportation Security Administration (TSA)
concept video created by CompEx Inc. that shows how citizens can be
tracked and monitored throughout an airport terminal -- without their
knowledge or consent.
The animated flash clip is posted on the authors' website at:
http://www.spychips.com/RFIDairport.html
In the video, citizen "Bob" is remotely identified and tracked via Radio
Frequency Identification (RFID) devices as he enters an airport and
navigates to his gate. The video ends with chilling frames of a
government agent surreptitiously scanning Bob and his belongings as he
sits in the waiting area.
CompEx Inc. President Aram Kovach, who developed the film as a demo for
the TSA, received a U.S. Patent for the idea he calls "Method for
Tracking and Processing Passengers and their Transported Articles" in
November of 2005. According to company press releases, TSA officials
entertained his ideas twice, once in 2002 and once in 2003, and "offered
to direct CompEx in pursuing a segmented objective within the guidelines
they have set forth."
"This footage raises the specter of Soviet-style government surveillance
creeping onto our free soil," said McIntyre. "People need to know that
our government has actively considered these disturbing and invasive
RFID concepts. With RFID now appearing in our passports, the threat to
our privacy and civil liberties may be more than theoretical."
"RFID passports will do little to keep us safer," Albrecht added. "On
the contrary, by requiring us to carry RFID tags in our travel
documents, the government is jeopardizing our personal information while
doing little to slow down the bad guys."
The new passports are vulnerable to hacking and cloning by criminals.
Last week at the Black Hat security conference in Las Vegas, German
researcher Lukas Grunwald showed how easily a criminal or terrorist
could clone RFID tags like those in U.S. passports using inexpensive and
readily available hardware.
================================================== ===================
ABOUT "SPYCHIPS"
Liz McIntyre and Katherine Albrecht are the authors of "Spychips: How
Major Corporations Plan to Track your Every Move with RFID." The book
draws on patent documents, corporate source materials, conference
proceedings, and firsthand interviews to paint a convincing -- and
frightening -- picture of the consumer privacy threat posed by RFID.
Despite its hundreds of footnotes and academic-level accuracy, the book
remains lively and readable according to critics, who have called it a
"techno-thriller" and "a masterpiece of technocriticism."
Two days prior to its release in 2005, "Spychips" flew the top of the
Amazon bestseller charts, hitting number one as a "Mover & Shaker,"
making its way to the top-ten Nonfiction bestseller list, and spending
weeks as a Current Events bestseller. In a nod to the book's focus on
freedom, Spychips was awarded the prestigious Lysander Spooner Award for
Advancing the Literature of Liberty and named "the year's best book on
liberty."
================================================== ===================
CASPIAN: Consumers Against Supermarket Privacy Invasion and Numbering
Opposing supermarket loyalty cards and other retail surveillance
schemes since 1999
http://www.spychips.com/
http://www.nocards.org/
You're welcome to duplicate and distribute this message to others who
may find it of interest.
================================================== ===================
Hyip, Hyip Forum, Real Hyip, Hyip Monitor, Hyip Investment, Best Hyip Forum - Powered by vBulletin
-
22-08-2006, 01:58 AM #6Senior Investor


- Join Date
- Jul 2005
- Location
- FREEDOMLAND
- Posts
- 3,277
- Feedback Score
- 0
- Thanks
- 574
- Thanked 2,129 Times in 355 Posts
 Privacy-Rights-Army.com
Privacy-Rights-Army.com
The problem is real!
Your car can testify against you, but your spouse can't.
This article is right on target! Only if we exert our rights will this kind of thing be stopped.
All media sources are working for us daily! Take advantage of it! Use this article to open a conversation about privacy!
Your PRIVACY is being VIOLATED EVERY DAY.............Only You DON'T KNOW IT.
http://Privacy-ACT-Facts.com
Quality copy attached
[IMG]aoladp://MA13895967-0002/time%2081406.jpg[/IMG]
[IMG]aoladp://MA13895967-0003/time%20pg2%2081406.jpg[/IMG]
-
22-08-2006, 02:28 PM #7Senior Investor


- Join Date
- Jul 2005
- Location
- FREEDOMLAND
- Posts
- 3,277
- Feedback Score
- 0
- Thanks
- 574
- Thanked 2,129 Times in 355 Posts
 Privacy Rights Army
Privacy Rights Army
AUG. 21 5:30 P.M. ET Two AOL employees were fired and its chief technology officer has left the company in the aftermath of a privacy breach that involved the intentional release of more than 650,000 subscribers' Internet search terms.
Although AOL had substituted numeric IDs for the subscribers' user names, the search queries themselves contained Social Security numbers, medical conditions and other data that could be traced to an individual. In fact, The New York Times was able to trace user 4417749 to Thelma Arnold, 62, of Lilburn, Ga. Maureen Govern, the technology chief, will be replaced on an interim basis by John McKinley, who had held that position before becoming AOL's president for digital services. The change takes effect immediately, according to a memo AOL Chief Executive Jonathan Miller sent to employees on Monday.
"This incident took place because some employees did not exercise good judgment or review their proposal with our privacy team," Miller said in a second memo. "We are taking appropriate action with the employees who were responsible."
The data release is among a series of breaches involving sensitive information in recent months. Unlike those resulting from computer hacking or missing laptops, however, the AOL data had been intentionally released as part of a program to assist academic researchers.
AOL, a unit of Time Warner Inc., apologized two weeks ago for what it termed a mistake made by a company researcher who had failed to properly seek clearances before releasing three months' worth of search data. Though the information was meant for researchers, it was released to a public site and quickly circulated once a blogger discovered it.
The company fired the researcher who released the data and that employee's direct supervisor, who reported to Govern, said one person familiar with the company's decisions. The person, who spoke on condition of anonymity because release of personnel information was not authorized, would not say whether Govern's departure was voluntary. The person also would not identify the two employees who were fired.
Although the search terms released were not directly tied to real names, many individuals type their own names to find out what's being said about them. They may later search for online mentions of their credit card or Social Security numbers and perhaps for prescription drug prices, revealing their medical ailments. All the searches for each user name were linked to the same numeric ID in the released data.
AOL removed the information from its site once senior executives learned of it, but by then copies already were widely available. Some people even created search sites just for the AOL data.
At least two groups have asked the Federal Trade Commission to investigate. In its complaint, filed last week, the Electronic Frontier Foundation accused AOL of breaking a promise to protect its subscribers' privacy.
Kevin Bankston, staff attorney with the EFF, said he hoped the breach would prompt Internet companies to be more forthcoming about what data they keep and for how long. Congress, he said, may need to intervene.
"Rearranging personnel is not going to get to the root of this problem, a problem which extends far beyond AOL and to the rest of the Internet industry," Bankston said. "As an industry, the search engines have been unacceptably tightlipped about what their practices are regarding search logs."
To prevent a recurrence, Miller said AOL will:
-- Create a task force led by senior executives to review privacy and data-retention policies.
-- Place additional limits on employee access to data, regardless of whether they are linked to individual accounts.
-- Evaluate technologies designed to flag sensitive information. Under such a system, for instance, a 16-digit string might be assumed to be credit card number and kept out of research databases.
-- Improve employee education and awareness on privacy.
The fallout occurs as AOL tries to lure more people to its search services and other free, ad-supported features to offset a revenue decline that's likely to accelerate as the company stops charging for AOL.com e-mail accounts and software.
AOL continues to rank fourth in search, behind Google Inc., Yahoo Inc. and Microsoft Corp.'s MSN, according to data released this week by Nielsen/NetRatings and comScore Media Metrix. Shares in Time Warner closed unchanged at $16.50 in Monday trading on the New York Stock Exchange.
-
22-08-2006, 07:28 PM #8Senior Investor


- Join Date
- Jul 2005
- Location
- FREEDOMLAND
- Posts
- 3,277
- Feedback Score
- 0
- Thanks
- 574
- Thanked 2,129 Times in 355 Posts
 Privacy Rights Army
Privacy Rights Army
Gov't: Carmakers Must Alert Consumers to Recorders in CarsTuesday, August 22, 2006

WASHINGTON — The government will not require recorders in autos but said on Monday that car makers must tell consumers when technology that tracks speed, braking and other measurements is in the new vehicles they buy.
The National Highway Traffic Safety Administration regulation standardizes recorder content and sets guidelines for how the information should be disclosed. It also requires recorders to be more durable.
Privacy experts complained that consumer interests are not fully protected and information captured by recorders can be exploited.
Click here to visit FOXBusiness.com's Autos Center.
Safety experts, consumer groups and insurance companies have long pressed the agency to mandate recorders in cars, but industry has responded voluntarily in recent years. About two-thirds of the new vehicles now produced each year contain the device that is connected to air bag systems. General Motors (GM) equips all its vehicles with recorders, a company spokesman said.
Regulators sought on Monday to set basic standards for their use, saying that uniform safety data will help make future auto safety regulation more precise.
Automakers have until September 1, 2010, to comply with the notification and other requirements in the new regulation, if they choose to equip their vehicles with recorders.
-
26-08-2006, 05:25 PM #9Senior Investor


- Join Date
- Jul 2005
- Location
- FREEDOMLAND
- Posts
- 3,277
- Feedback Score
- 0
- Thanks
- 574
- Thanked 2,129 Times in 355 Posts
 Privacy Rights Army
Privacy Rights Army
RFID, its implications and how to defeat
by Jon Winthrop
Imagine a future in which your every belonging is marked with a unique number identifiable with the swipe of a scanner, where the location of your car is always pinpoint-able and where signal-emitting microchips storing personal information are implanted beneath your skin or embedded in your inner organs.
This is the possible future of radio frequency identification (RFID), a technology whose application has so far been limited largely to supply-chain management (enabling companies, for example, to keep track of the quantity of a given product they have in stock) but is now being experimented with for passport tracking, among other things. RFID is set to be applied in a whole range of consumer settings. Already being tested in products as innocuous as shampoo, lip balm, razor blades, clothing and cream cheese, RFID-enabled items are promoted by retailers and marketers as the next revolution in customer convenience. Consumer advocates say this is paving the way for a nightmarish future where personal privacy is a quaint throwback.
How RFID works
There are two types of RFID tags: active and passive. When most people talk about RFID, they talk about passive tags, in which a radio frequency is sent from a transmitter to a chip or card which has no power cell per se, but uses the transmitted signal to power itself long enough to respond with a coded identifier. This numeric identifier really carries no information other than a unique number, but keyed against a database that associates that number with other data, the RFID tag's identifier can evoke all information in the database keyed to that number.
An active tag has its own internal power source and can store as well as send even more detailed information.
The RFID value chain involves three parts: the tags, the readers and the application software that powers these systems. From there, the data generated by the application software can interface with other systems used in an enterprise, or, if they obtain the information or collect it themselves, concievably by governments or more nefarious organizations.
Where it’s used today
Global companies such as Gillette, Phillips, Procter & Gamble, Wal-Mart and others see huge savings to be made from the use of RFID, and there are numerous pilot projects underway which are indicating savings in supply chains as well as the ability to add value to both product owner, product reseller and customer.
But they’re just pilots, mostly. RFID is a long way from being everywhere, so far. Pharmaceutical tracking has long been held out as one of the flagship applications of RFID in the short term, yet just some 10 medications are expected be tagged using RFID technology on a large scale in the U.S. during 2006, analysts predict. Slow roll-outs are contrasting sharply with the optimism of a year ago, when evidence suggested tripling or even quadrupling of RFID for consumer goods tracking. Why? Uncertainty over pending legislation. There are a complex mixture of federal and new state laws (in particular Florida and California) intended to combat drug theft and counterfeiting that have implications for RFID. The details are still being worked out.
Where it’s likely to be used tomorrow
Depending which analysts you believe, the market for RFID technology will represent between 1.5 and 30 Billion USD by the year 2010. Analyst firm IDTechEx, which tracks the RFID industry, believes more than 585 billion tags will be delivered by 2016. Among the largest growth sectors, IDTechEx forsees the tagging of food, books, drugs, tires, tickets, secure documents (passports and visas), livestock, baggage and more.
Buses and subways in some parts of the world are being equipped with RFID readers, ready for multi-application e-tickets. These are expected to make things easier for the commuter, and help stem the fraud from the current paper-ticket system. However the biggest problem facing rollouts of RFID for commercial micropayment tracking is apparently not technical, but involves agreeing on the fees charged by the clearing house and how credit from lost and discarded tickets will be divided.
Passport tracking
One of the highest profile uses of RFID will be passport tracking. Since the terrorist attacks of 2001, the U.S. Department of Homeland Security has wanted the world to agree on a standard for machine-readable passports. Countries whose citizens currently do not have visa requirements to enter the United States will have to issue passports that conform to the standard or risk losing their non-visa status.
American and other passports are being developed that include RFID-based chips which allow the storage of considerable amounts of data such as fingerprints and digitized photographs. In the U.S., these passports are due to start being issued in October of 2006. Early in the development of these passports there were gaping security holes, such as the capability of being read by any reader, not just the ones at passport control (the upshot of this was that travelers carrying around RFID passports would have been openly broadcasting their identity, making it easy for wrongdoers to easily – and surreptitiously – pick Americans or nationals of other participating countries out of a crowd.)
Those security blunders were initially corrected by adding metal shielding to the passport cover to minimize its readability when closed, dialing back the range of the electronics and adding a special electronic protocol called Basic Access Control (or BAC). This scheme required the passport to be opened and scanned before its data could have been properly interpreted by an RFID receiver. Unfortunately, in early February 2006, Dutch security experts managed to “listen in” on the communications between a prototype BAC-protected passport and a receiver and cracked the protocol. Which means the international authority developing this new global passport standard may need to go back to the drawing board as of this writing, because ‘bad guys’ could clearly stand in line at passport control and capture passport information. Details of the Dutch hack here.
Implications for privacy seekers
RFID has clear implications for those who are worried about their privacy and safety. Some of them are obvious, and some of them are not.
- Can be read without your knowledge – Since the tags can be read without being swiped or obviously scanned (as is the case with magnetic strips or barcodes), anyone with an RFID tag reader can read the tags embedded in your clothes and other consumer products without your knowledge. For example, you could be scanned before you enter the store, just to see what you are carrying. You might then be approached by a clerk who knows what you have in your backpack or purse, and can suggest accessories or other items.
- Can be read a greater distances with a high-gain antenna – For various technical reasons, RFID reader/tag systems are designed so that distance between the tag and the reader is kept to a minimum. However, a high-gain antenna can actually read tags from much further away, leading to privacy problems. Governments or others could punch through privacy screens and keep tabs on people.
- Difficult to remove – RFID tags are hard for consumers to remove; some are very small (less than a half-millimeter square, and as thin as a sheet of paper) - others may be hidden or embedded inside a product where consumers cannot see them. New technologies allow RFID tags to be printed right on a product and may not be removable at all
- Disruptions if maliciously jammed – RF signals can be jammed, which could complicate everyday life if RFID tags became essential. Imagine a central bus or train station, maybe an airport, where suddenly everyone could neither be ID'd or access their cash accounts. A single hour of jamming during morning rush over a large area could cost a large city untold millions of dollars in delayed commerce and transport. It would be worse than a mass-transit strike, and easier to repeat.
- Could be linked to a credit card number – The Universal Product Code (UPC) implemented with barcodes allows each product sold in a store to have a unique number that identifies that product. Work is proceeding on a global system of product identification that would allow each individual item to have its own number. When the item is scanned for purchase and is paid for, the RFID tag number for a particular item can be associated with the credit card number it was purchased with.
- Potential for counterfeit – If an RFID tag is being used to authenticate someone, anyone with access to an RFID reader can easily capture and fake someone else’s unique numeric identifier, and therefore, in essence, their electronic 'signature'. If an RFID-tagged smartcard is used for shopping, for instance, anyone who intercepted and reverse-engineered your number, and programmed another card with it, could make charges on your account.
- Marking for crime – Even after you leave a store, any RFID devices in things you buy are still active. A thief could walk past you in the mall and know exactly what you have in your bags, marking you as a potential victim. Someone could even circle your house with an RFID scanner and pull up data on what you have in your house before robbing it. As a result, there are now discussions of “zombie” RFID tags that expire upon leaving the store and reanimate if the product is ever returned to the store and returned to the supply chain.
- Marking for violence – Military hardware and even clothing are beginning to make use of RFID tags to help track these items through supply chains. RFID is being used today by the U.S. military to track materials in Iraq and Afghanistan. Some analysts are concerned about particular items being associated with high-level officers that could trigger roadside bombs via an RFID scan of cars going by. (Thankfully, RFID tags retained close to the body can rarely be scanned. For instance, UHF tags, the kind being most widely deployed, are virtually unreadable near the body because of its high water content.)
What makes RFID a more significant privacy threat than mobile phones is the fact that readers will be readily available and ubiquitously deployed. In other words, RFID readers will soon be an accepted element of everyday life, while eavesdropping equipment for mobile phones is unlikely to be.
How to thwart RFID technology
There are a few approaches you can take to thwart RFID tags … but before you take proactive steps, note that sometimes the very absence of a tag or its signal in places it’s expected could arouse suspicion. For instance, if you’re carrying what is expected to be an RFID-tagged passport and your tag isn’t working, say, you may invite unwanted scrutiny. Be careful which tags you choose to disrupt.
The simplest, most permanent approach to disable RFID tags is to destroy them. If you can detect them and wish to permanently render them useless, remove them and smash the small chip component with a hammer. If you’re not sure whether a product you own contains a tag, consider putting it in a microwave to destroy the tag if the object is otherwise safe to be microwaved. Be careful with some plastics. Note there have been reports of RFID materials catching fire in microwaves.
If removing the tag is not practical, there are four general ways to disrupt RFID tag detection.
- Blocking – Construct a conductive foil box (even tin foil is good) around the tag. If you are concerned about RFID emissions from work badges, school IDs, new generation drivers licenses, credit cards, and even cash in the future containing RFID tags, buy or make an RFID-proof wallet. RFID wallet project details are easy to find on the Internet.
- Jamming – Since RFID systems make use of the electromagnetic spectrum like wireless networks or cellphones, they are relatively easy to jam using a strong radio signal at the same frequency the tag operates. Although this would only be an inconvenience for consumers in stores (longer waits at the checkout), it could be disastrous in other environments where RFID is increasingly being used, like hospitals, or in military combat situations. Such jamming devices, however, would in most cases violate government regulations on radio emissions. A group of researchers in Amsterdam have theorized that a personal RFID jammer is possible (read their paper here) but the device seems only theoretical at this time.
- Repeated interrogation – Active RFID tags that use a battery to increase the range of the system can be repeatedly interrogated to wear the battery down, disrupting the system.
- Popping – Generating a very strong pulse of radiation at the right frequency can cause RFID tags to resonate and break.
Related Content
ICAO specification for BAC passport protection algorithm
Details of Dutch crack of e-passport algorithm
Cell phone hazards
RFID Guardian: A battery-powered mobile device for RFID privacy management
-
Sponsored Links
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
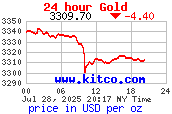
24 Hour Gold
Advertising
- Over 20.000 UNIQUE Daily!
- Get Maximum Exposure For Your Site!
- Get QUALITY Converting Traffic!
- Advertise Here Today!
Out Of Billions Of Website's Online.
Members Are Online From.
- Get Maximum Exposure For Your Site!
- Get QUALITY Converting Traffic!
- Advertise Here Today!
Out Of Billions Of Website's Online.
Members Are Online From.






 LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks



 Reply With Quote
Reply With Quote