When entering into trade by commodity, to make things easier, it is better to ensure that there is proper security in the data lines. This will help to prevent under quoting of prices for a particular commodity. Internet technologies have helped to make things better. Software systems are now available that will properly secure your system.
How does the system function? Typically, firewalls check the Internet Protocol (IP) address of the origin of the data packet to authorize its entry into the system. The IP address checks are also performed by the firewall when a data packet is sent to a destination on the Internet. Thus, the 'firewall' restricts access to certain IP addresses and verifies that the internet address of each incoming/outgoing message is legitimate with its source and if so, the message is allowed to pass through.
The list where the address is clarified is called 'the approval list'. A firewall features two key components: gates and chokes. Gates allow data to pass between two networks. Chokes block incoming packets not destined for the gate and block outgoing packets not coming from the gate. In this way, any packet that does not have the gate address in its origin or destination address is blocked. The gate is typically a gateway and the choke an intelligent router located between the gate and the external network.
An IT application is mainly used with reference to client-server development. Web-based applications are referred to as applications but reside on the intranet and are protected by security measures at the client-server and database levels. Some intranets protect their internal applications using second level firewall security.
For example, an HTTP (Hyper Text Transfer Protocol) request by an investor for a public Web page will be honored, whereas an FTP (File Transfer Protocol) request to a host (computer) behind the firewall may be dishonored.
A single firewall may be sufficient for most business systems but critical applications may require multiple firewalls to reduce the risk of hackers making entry into the system. Internet trading applications store private data behind firewalls to allow only authorized personnel to have access to it.
Please visit our sponsors
Results 1 to 1 of 1
-
09-07-2010, 05:01 AM #1Junior Member

- Join Date
- Jul 2010
- Posts
- 1
- Feedback Score
- 0
- Thanks
- 0
- Thanked 0 Times in 0 Posts
 Simple network firewall: router only permits traffic to/from host through secure lines
Simple network firewall: router only permits traffic to/from host through secure lines
-
Sponsored Links
-
Sponsored Links
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
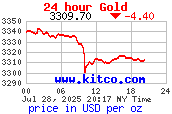
24 Hour Gold
Advertising
- Over 20.000 UNIQUE Daily!
- Get Maximum Exposure For Your Site!
- Get QUALITY Converting Traffic!
- Advertise Here Today!
Out Of Billions Of Website's Online.
Members Are Online From.
- Get Maximum Exposure For Your Site!
- Get QUALITY Converting Traffic!
- Advertise Here Today!
Out Of Billions Of Website's Online.
Members Are Online From.






 LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks


 Reply With Quote
Reply With Quote